Understanding Audit Reports and Requiring Two-Factor Authentication for Package Publishing and Settings Modification
Audit reports usually contain tables of information about security vulnerabilities in your project's dependencies, this is to enable you fix the vulnerability or troubleshoot further.
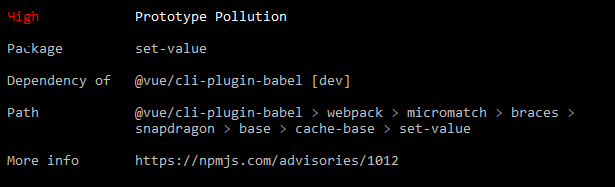
Vulnerability table fields
- Severity
- Description
- Package
- Patched in
- Dependency of
- Path
- More info
Severity
The severity of a vulnerability is determined by the exploitability and impact of the vulnerability in its most common use case.
| Severity | Recommended action |
|---|---|
| Critical | Address immediately |
| High | Address as quickly as you can |
| Moderate | Address as time permits |
| Low | You should address at your own discretion |
Description
This is the description of the vulnerability. For instance, "Denial of service".
Package
This is the name of the package that contains the vulnerability.
Patched in
This represents the semantic version range that describes which versions contain a fix for the vulnerability.
Dependency of
This is the module that the package with the vulnerability depends on.
Path
This is the path to the code that contains the vulnerability.
More info
This is usually a link to the security report.
Requiring two-factor authentication for package publishing and settings modification
As a package publisher, if you want to protect your packages, you can require that everyone who has a write access to a package provide a one-time password in addition to their login token once they publish the package to the registry or modify package settings.
To be able to modify or publish a package with two factor authentication (2FA) enabled, a publisher has to have 2FA enabled on their user account with Authorization and publishing selected.
It should be noted that currently, it is not possible to publish a package with 2FA enabled on CI. If you want more secure CI publishing, you should enable 2FA on the npm account used for CI, and then select Authorization only, and finally, you should create a CIDR-restricted token for CI (find out more about this in our tutorial on working with security tokens).
- Sign in to https://www.npmjs.com/.
- Navigate to the package which you want to require a second factor to publish or modify settings.
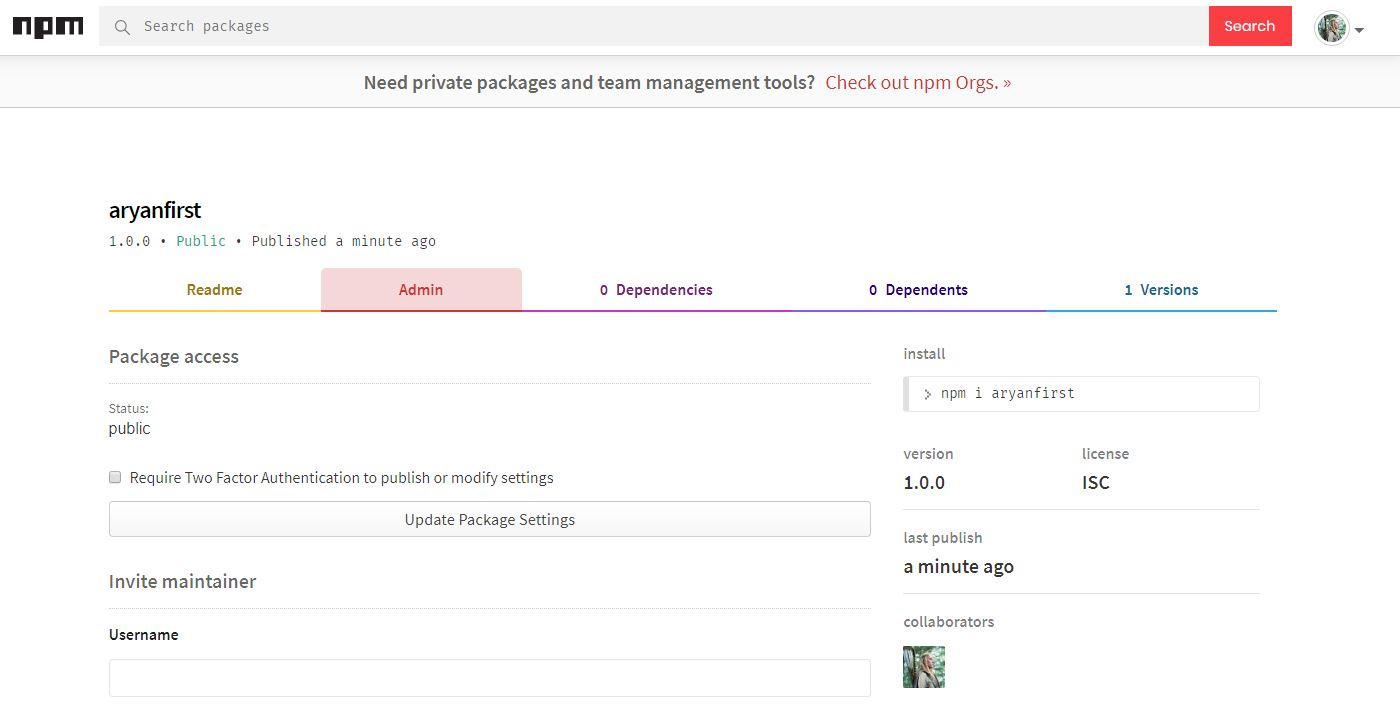
- Then click Admin.
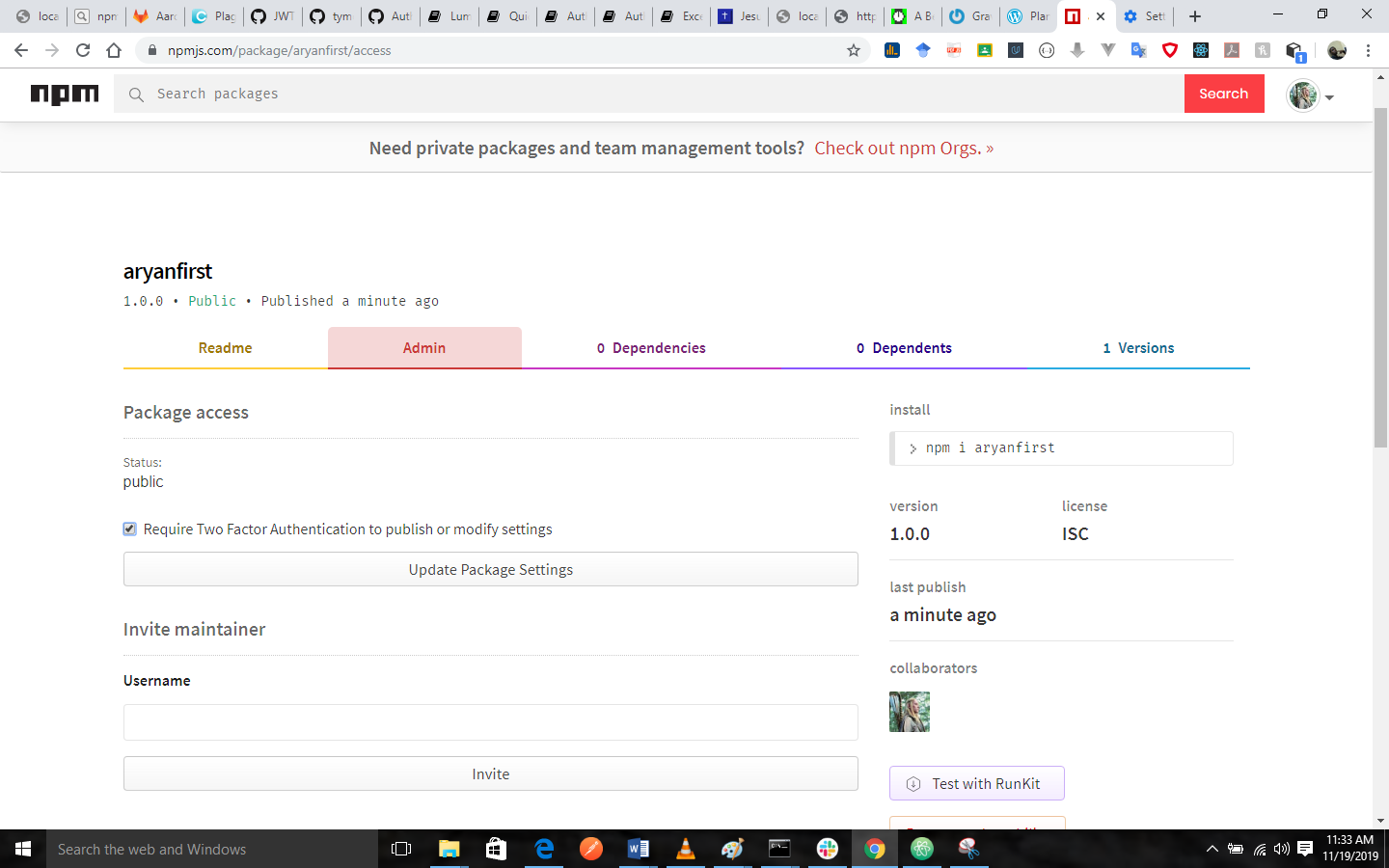
- In the "Package Access" section, you should select "Require Two Factor Authentication to publish or modify settings"
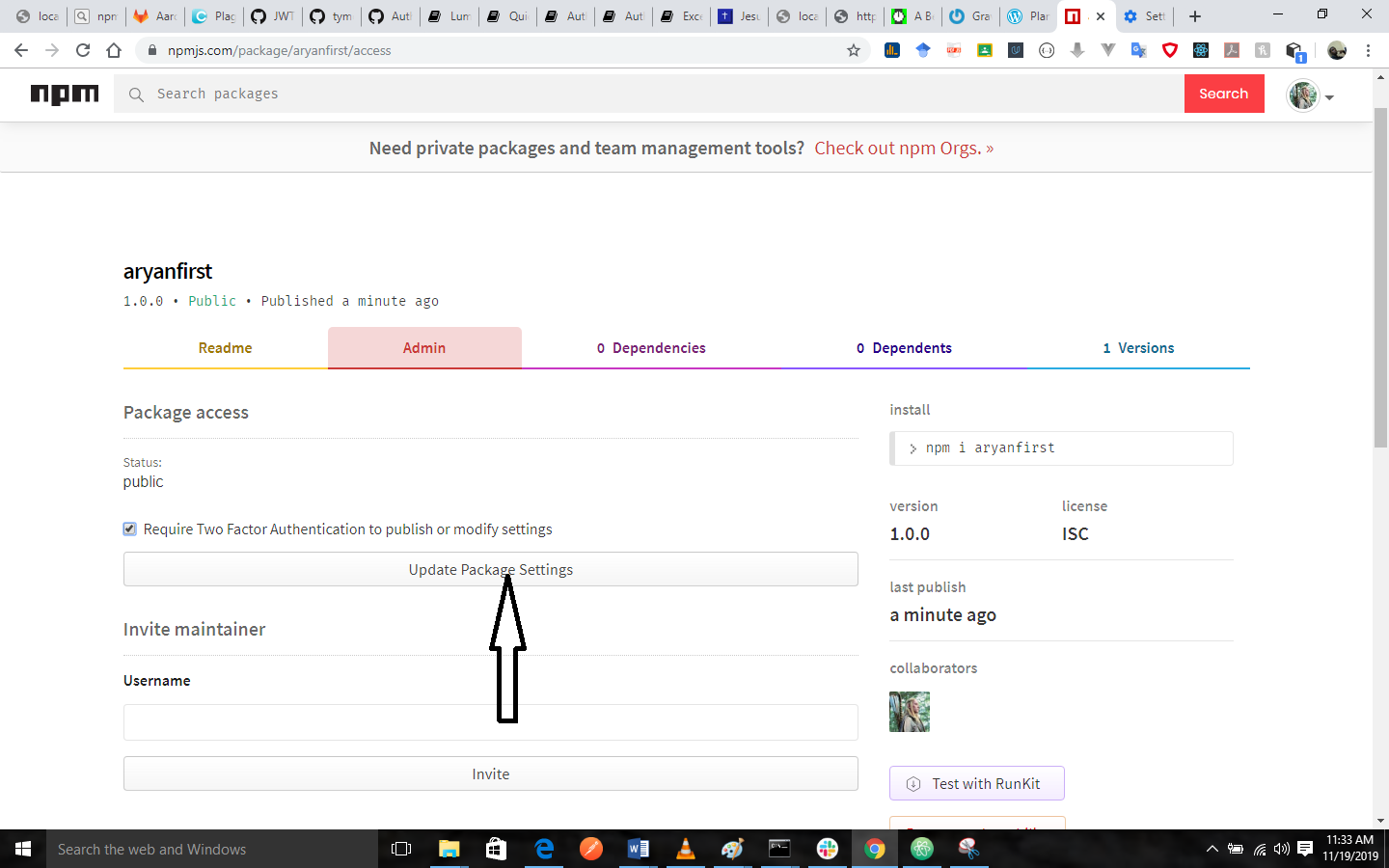
- Once you are done with making these changes, you should click on update package settings
Previous:
How to run a security audit with npm audit.
Next:
Working with Private npm Packages: Setup, Publishing, and Access Control.
